Risk of ransomware attack faced by enterprises
Every day, we hear news reports about companies of all sizes becoming the latest victims of ransomware attacks on their IT infrastructure, causing disruption to their services for internal employees and external customers, and potentially costing them a large sum of money as ransom to the attacker to be able to recover their own data. In the worst-case scenario, the business is forced to close because they can’t afford to pay the ransom and the return is just not worth it. Even if the organisation can afford to pay the ransom to recover its data, certain variants of the malware prevent data recovery by encrypting the data and discarding the key. Only 29 percent of victims were able to recover all of their data after an assault, according to a global study.
As the above image reminds us, every company must treat a ransomware attack as a disaster and thoroughly assess the risk, strategize the solution, technology, and processes needed to manage the disaster, and plan for recovery.
What is immutable?
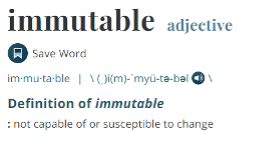
Immutable, according to the Merriam-Webster definition, refers to something that is not capable of or susceptible to change. So, in the IT world, if a piece of data is saved in an immutable storage, that data is protected from deletion and modification. Having an immutable copy of any static data, whether online or backup and archive data, means that the company will have a copy of the data that can be used for service recovery in the event of a ransomware attack on the online production storage.
Why are enterprises asking for it?
According to local cybersecurity firm TrendMicro, they detected 113,010 ransomware threats in Malaysia in the first 4 months of 2021, that is equivalent to almost 950 cases a day. (Source: https://www.thestar.com.my/tech/tech-news/2021/08/02/standing-up-to-ransomware). The number of malwares detected increase by 160% y-o-y for the first half of 2021 compared to the year 2020.
Due to the critical nature of data for the business continuity of the organization, the CIO/CTO will need to ensure that there is a plan for prevention and also a process and solution to be able to recover after an attack.
How does it work?
The backup data will be transmitted to a repository running on a hardware agnostic Veeam supported Linux distribution. This Linux distribution is also hardened; even the system administrator and backup administrator are unable to erase backup data.
The Linux hardened repository will be presented to the backup software as a backup capacity, and by configuring the policy, schedule, and backup set, the enterprise can selectively configure mission and business critical data to be backed up into immutable storage, protecting it against scenarios such as accidental deletion and modification, data corruption due to hardware failure, and, most importantly, malicious software or rogue administrators that delete or modify the backup data.
As a backup administrator, there are no major differences in terms of setting up the backup job. The Linux immutable depository will be presented just like any other backup repository. The immutability of the backup data can be configured to any length of time (7 days by default) but it can be modified to fit the IT data protection policy of the organization.
What is AVM Cloud offering?
For enterprises and businesses that like to take advantage of these services, there are a few approaches to this. The first approach is to subscribe to an on-prem private cloud backup solution, where the cloud service provider will setup an on-prem backup server and sufficient storage on a rental basis. The backup software can perform backups locally on bare metal servers, servers and applications as well as VMs. For long term retention of backup data, the older backup copy can be archived to the cloud.
The second approach is for customers who have already migrated their infrastructure to the cloud. Customers can subscribe to backup services and specify the amount of data to be stored in immutable storage for additional protection.
This is in line with the common backup best practise of the 3-2-1 rule, where data needs to be stored in 3 different copies of the data, on two different media, and with one copy stored offsite. Now with the services, the onsite and offsite copies are immutable.
With all being said, the solutions and technologies described here are to provide a backup copy which is not affected by malware to be able to restore it for service resumption, either from a local or remote repository. But the enterprise and businesses still need to have preventive solutions and products implemented as well as security processes and procedures in place to prevent attacks from even happening.